Saturday, 30 June 2012
Top 10 New Release Laptops Of 2012
Hello friends in my today's post i made a collection of top 10 new releases laptops of 2012.
Labels:
Gadgets,
Tips and Tricks
Best Methods For Copy Fast any Easy
 Copying File is so boring and slow process. Windows File Transfer System is so Slow, It takes lots of time. Sometimes it give us pain. But now you can supercharge the simple act of copying and pasting.
Copying File is so boring and slow process. Windows File Transfer System is so Slow, It takes lots of time. Sometimes it give us pain. But now you can supercharge the simple act of copying and pasting.
Today i have 3 apps to make this process super fast. These include transfer resuming, copy speed computation and control, improved copy progress display, copy list editable while copying, copy list saving/loading, and an error log. So Here is the Apps:
Labels:
PC Softwares,
PC Tricks
Wednesday, 27 June 2012
How to Hide the drives(c:,d:,e:,...etc) in Ur Computer
Labels:
PC Tricks
Thursday, 21 June 2012
How To Unlock Huawei E1550 Idea Netsetter 3G
 Add the first PC to your modem, connect the modem to install the software automatically opens the make install.
Add the first PC to your modem, connect the modem to install the software automatically opens the make install.
1 -Here's one of the tools to Download.These tools will tell you your USB modem unlock code and flash code.
How To Protect Yahoo! & Gmail Accounts From Hackers
In this post I will tell you Guys how to Protect it From Hackers...
Security of your Gmail and Yahoo account is very important
matter. Think what happens if someone hacked your gmail a/c password. However
by default gmail and Yahoo has many built-in security features to provide good protection
to your account but many Gmail A/C’s are HiJacked by Hackers due to mistakes of
users.
Labels:
Hacking,
Security,
Tips and Tricks
Tuesday, 19 June 2012
Samsung Mobile Secret Codes – Updated
Do you have any Samsung Mobile? if yes then here is a list of updated Samsung Mobile Secret Codes. These secret codes should work for all samsung mobiles. Using these secret codes you can easily navigate to your mobile functions like on/off bluetooth,delete all the messages from your inbox, enabled or disabled phone lock and lot other functionality.
Monday, 18 June 2012
Now active your windows as genuine (windows 7)
If your windows show this error message that your windows is not
genuine, just download this software and make your windows as genuine.
Download this software and run this, then Click Install wait few minutes
and restart your computer. That's it. Your computer is now genuine.
How to Trace Someones Details?
Today i am going to show you how to Track some one Details like IP address,OS,Browser of victims computer,Location,Net Useretc.,
then follow these Steps...
1)Click here to go to the site
Labels:
Hacking
Wednesday, 13 June 2012
Gmail Privacy Attack
You meet an old friend online on Gmail after a long time and you start chatting with that person.. and suddenly he/she says that they got to leave and goes offline...the chat box displays that the person is offline!!!
You are now left in a curiosity to know if that person had really signed out or just invisible!!!!
Labels:
Hacking
Tuesday, 12 June 2012
How to Identify Fake mails.
 In mu last post I have shown you guys how to send fake mails,here I will show you how to Identify them.
In mu last post I have shown you guys how to send fake mails,here I will show you how to Identify them.
More Interested to learn how to Identify the fake mails.Then follow these..
Open the mail that you want to find wheather it is real or a fake one..
In deep to explain you guys, I have sent a fake mail to my gmail account nasasrkr@gmail.com from emkei's Fake Mailer
Labels:
Fake mails,
Hacking
Sunday, 10 June 2012
Partitioning Hard disk in Windows7 without formatting
Steps for Partitioning :-
How to Send Fake Mails???
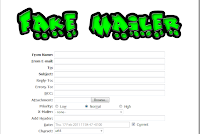 When it comes to anonymity, we are all interested as it counts in computer security also mailing can be fun and also be a prank, i strongly recommend EMKEI's mailer to be the best fake mailer to use, here, you can send free anonymous email to any account and can make the recipient see you to be any sender you want, like the government of America or a principal of your college or any thing else.
When it comes to anonymity, we are all interested as it counts in computer security also mailing can be fun and also be a prank, i strongly recommend EMKEI's mailer to be the best fake mailer to use, here, you can send free anonymous email to any account and can make the recipient see you to be any sender you want, like the government of America or a principal of your college or any thing else. With this you can make prank your friends...
Labels:
Fake mails,
Hacking
Saturday, 9 June 2012
Mystery behind 32-bit and 64-bit windows OS
This is one of the top FAQ questions asked by our newbie readers in windows. Windows always come in two versions named 32 bit and 64 bit. Most people don’t know the difference between the 32-bit and 64-bit obviously because 64-bit version had never came in the picture much since hardware in earlier times wasn’t so cheap as it is today. I will simply explain why I am relating 64-bit with hardware. But, first let us see what is the difference between 32-bit and 64-bit.
All about IP address
i am starting my hacking related posts with IP address.
In this post i have written all the basic concepts of IP addresses.
My next post will be on hacking IP address of a remote computer.
So before that lets have a glance at the basics of IP..
Labels:
Hacking
Tips to Improve Your Laptops Battery Life
.jpg) Do you know that there are billions of computer users in the world and a very large percentage of them are laptop users? Out of every 10 computer users 7 users use laptop. If you use your laptop on battery power, you’ll know how annyoing it is to lose battery power at the “worst time”. There are some guidelines that, if followed can help in improving the battery performance and keep it long lasting.
Do you know that there are billions of computer users in the world and a very large percentage of them are laptop users? Out of every 10 computer users 7 users use laptop. If you use your laptop on battery power, you’ll know how annyoing it is to lose battery power at the “worst time”. There are some guidelines that, if followed can help in improving the battery performance and keep it long lasting.Friday, 8 June 2012
The Hacker's Introduction
 Who is a hacker?
Who is a hacker?In computer security and everyday language, a hacker is someone who breaks into computers and computer networks.
A Hacker is a person who attacks on other's computers to spoil their system(generally).
Why do they hack?
Some people do hack to show their knowledge and skills. some people to take the revenge.
Labels:
Hacking
Thursday, 7 June 2012
How to Protect Yahoo Account from Hackers
2 Step verification or Second Sign-In verification is an addtional layer of security that protects your account even if your password gets hacked.This feature is already available for facebook and Gmail accounts .Yahoo has also launched Second Sign-In verification for accounts of selected countries (U.S, Canadian, Indian, Philippines).It is expected to be rolled out for all users by March 2012.
Labels:
Security
Wednesday, 6 June 2012
How to use pendrive as ram memory in windows 7
Hi friends, Windows 7 and Windows vista comes with a ready boost option. Q-What is ready boost
Ans- "ReadyBoost is a disk cache component of Microsoft Windows, first introduced with Microsoft'sWindows Vista in 2006 and bundled with Windows 7 in 2009. It works by using flash memory, a USB flash drive,SD card, CompactFlash, external hard drive.
Tuesday, 5 June 2012
Monday, 4 June 2012
Get Live Cricket Scores On Your Desktop Free
Labels:
PC Softwares
Sunday, 3 June 2012
How to install windows 8
Downloading the 2.5GB ISO image from Microsoft's website took me
about 20 minutes, although that time can extend based on your
Internet connection.
First up, a betta fish (because it's a beta, after all)
Internet connection.
First up, a betta fish (because it's a beta, after all)
Subscribe to:
Comments (Atom)

















